So you have been evaluating the new Tanzu for vSphere VM Service for some time and you want to start to integrate it into your CI/CD Pipelines? Well you have come to the right place.
In this guide I will show you how to configure Jenkins to use the VM Service in your Pipelines. This way you can use both traditional VM’s along side containers using Jenkins Pipelines.
Updated 7/12/21 with help from @fannystrudel to add credentials store and parameterize it as well as add the API Server Certificate! So much cleaner and secure now! Huge thank you to Fanny!
Pre-Reqs
- vSphere 7.0.2 with Workload Management Deployed see guides here
- A namespace deployed and the VM Service Configured see guide here
- A working template configured and tested that it deploys see guide here
- Jenkins Jenkins 2.289.2 or higher deployed, i used the container here
- Connectivity from Jenkins to your Supervisor Cluster API IP address
- A Jenkins Service account created, I used jenkins@vsphere.local but you could also use and SSO user.
- A quite place where you will not be interrupted see my guide here
Login to vCenter and go to Workloads then click your Namespace that is configured for the VM Service
Under Permissions Click on Manage Permissions
Now click add user
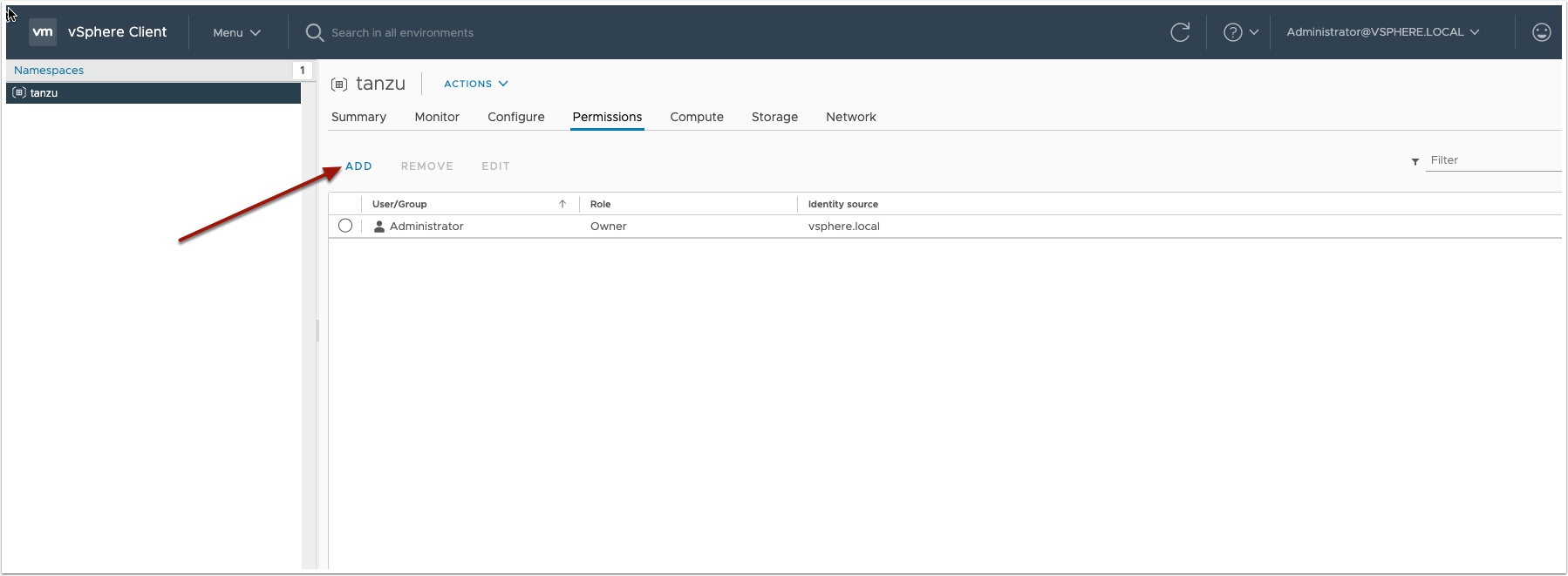
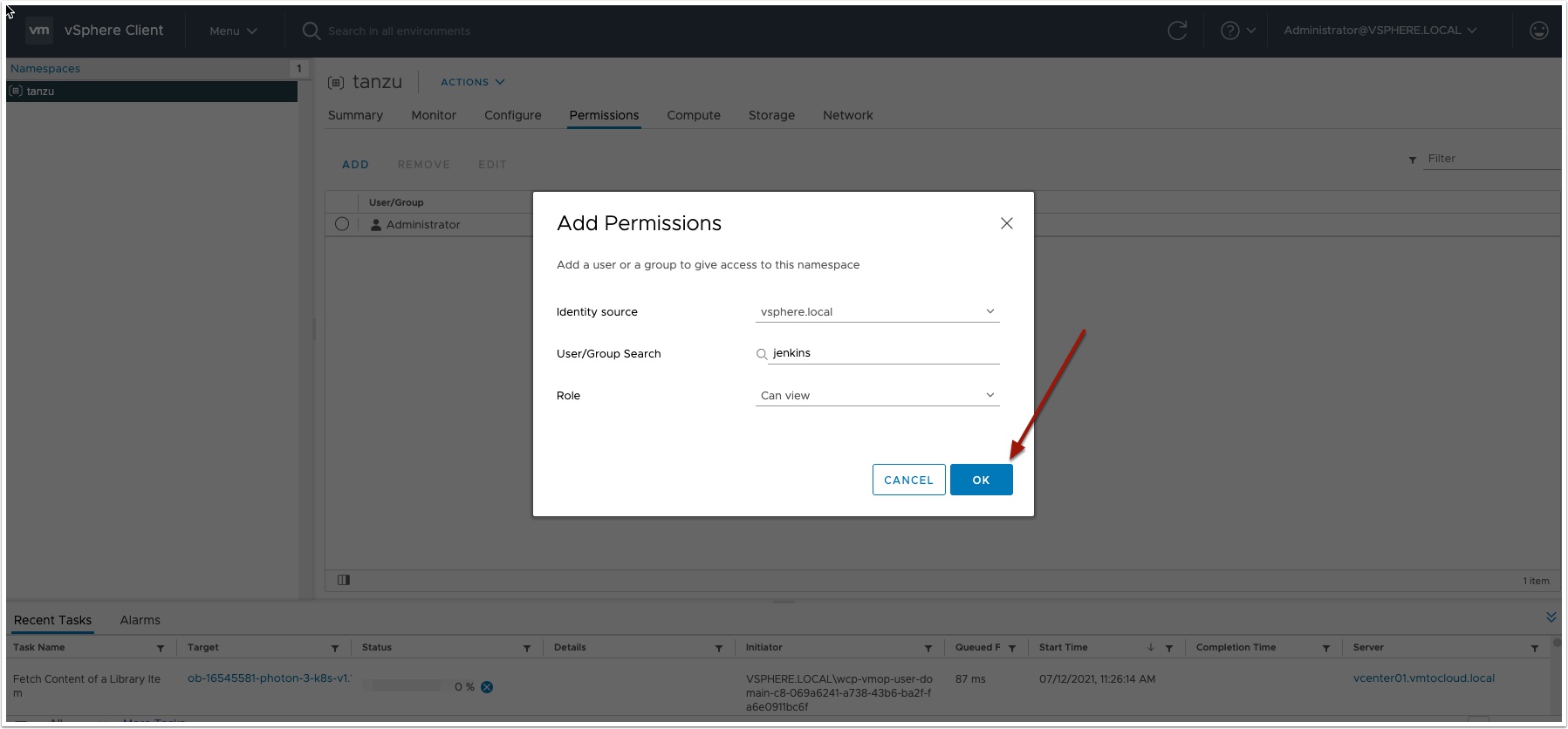
Add the Jenkins user you created for your service account
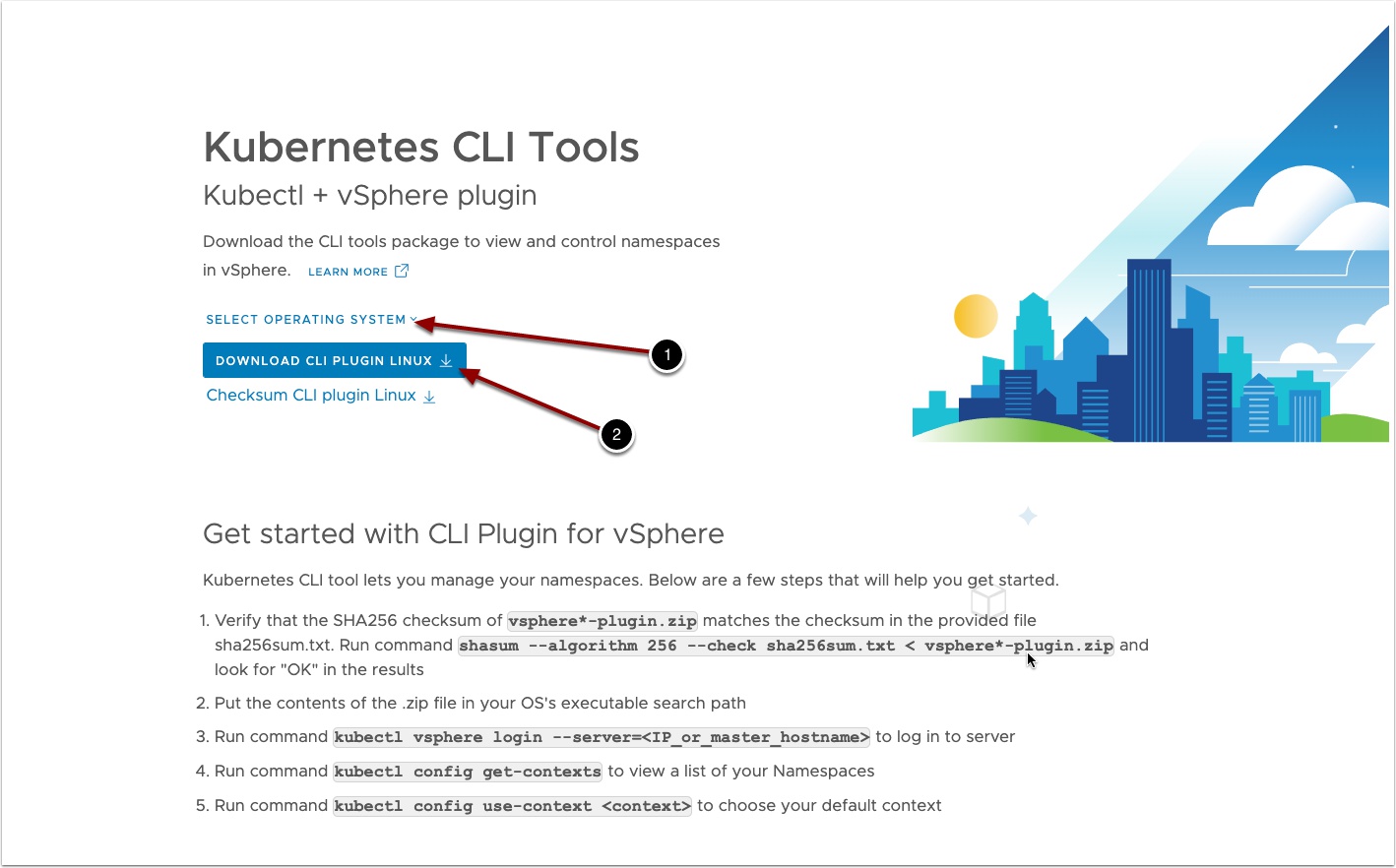
Now go back to Summary and Under Link to CLI tools Click Open
- Change Operating system to Linux
- Download the CLI tools locally and unzip them
docker cp /usr/local/bin/kubectl ContainerID:/usr/local/bin/kubectl
docker cp /usr/local/bin/kubectl-vsphere ContainerID:/usr/local/bin/kubectl-vsphere
Now grab the SSL certificate from the API server, this is the same IP address you just downloaded the CLI tool from.
echo quit | openssl s_client -showcerts -servername 192.168.110.200 -connect 192.168.110.200:443 > cacert.pem
Now copy that cert to the Jenkins servers /etc/ssl/certs directory if using the container you can do the following:
docker cp /home/cacert.pem ContainerID:/home/cacert.pem
Now let’s start configuring Jenkins. First we will create a new credential and store the username and password there, this way it is not in clear text and you can change it once here instead of all your pipelines.
Login to Jenkins and click Manage Jenkins and then Manage Credentials
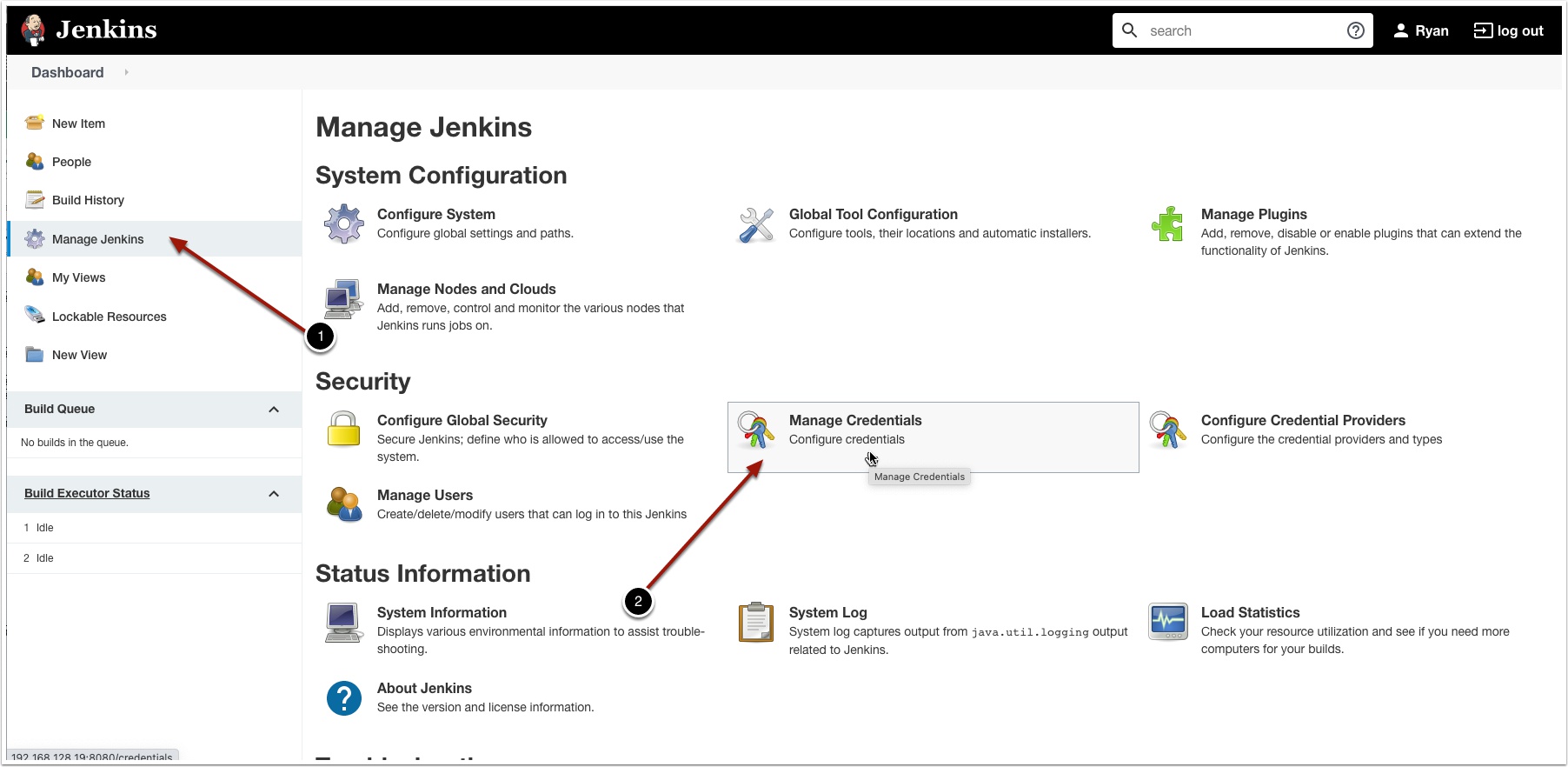
Now click Jenkins
Now click Global Credentials
Now click add credentials
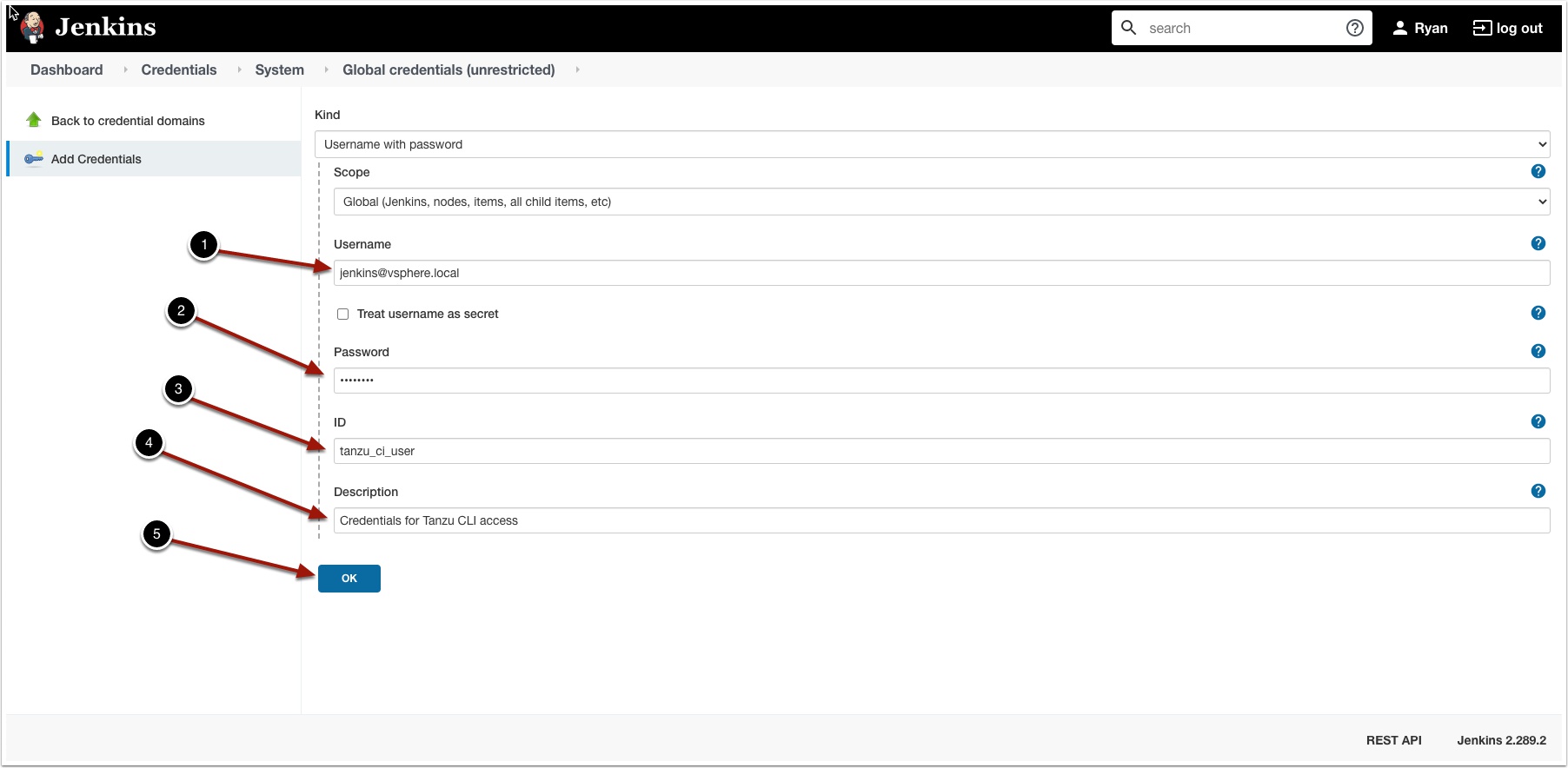
Now add the Jenkins user as shown
- The user name: jenkins@vsphere.local
- The password
- enter and ID: I used tanzu_ci_user
- Enter a description
- Click OK
Click Dashboard to go back to the main menu
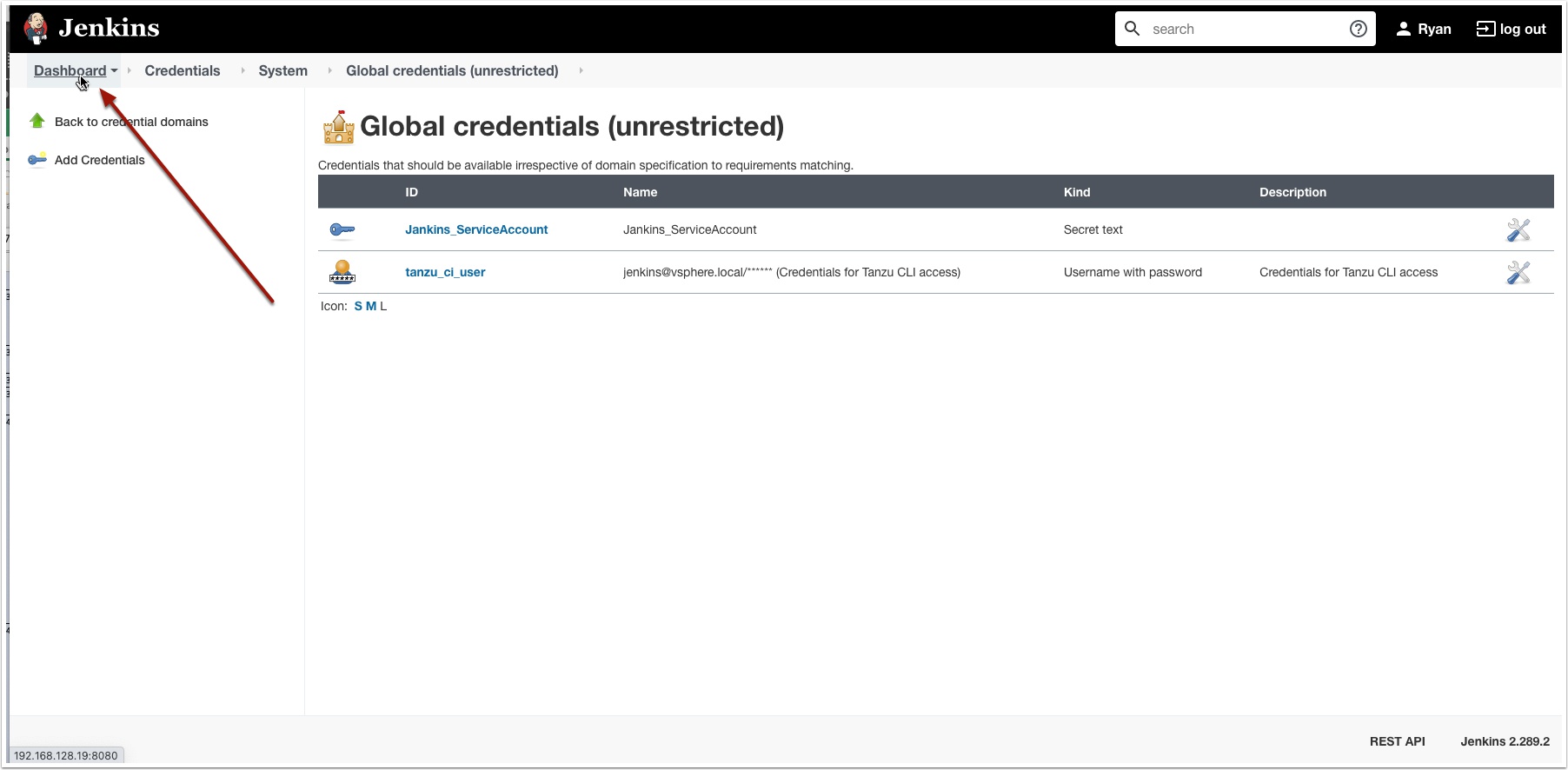
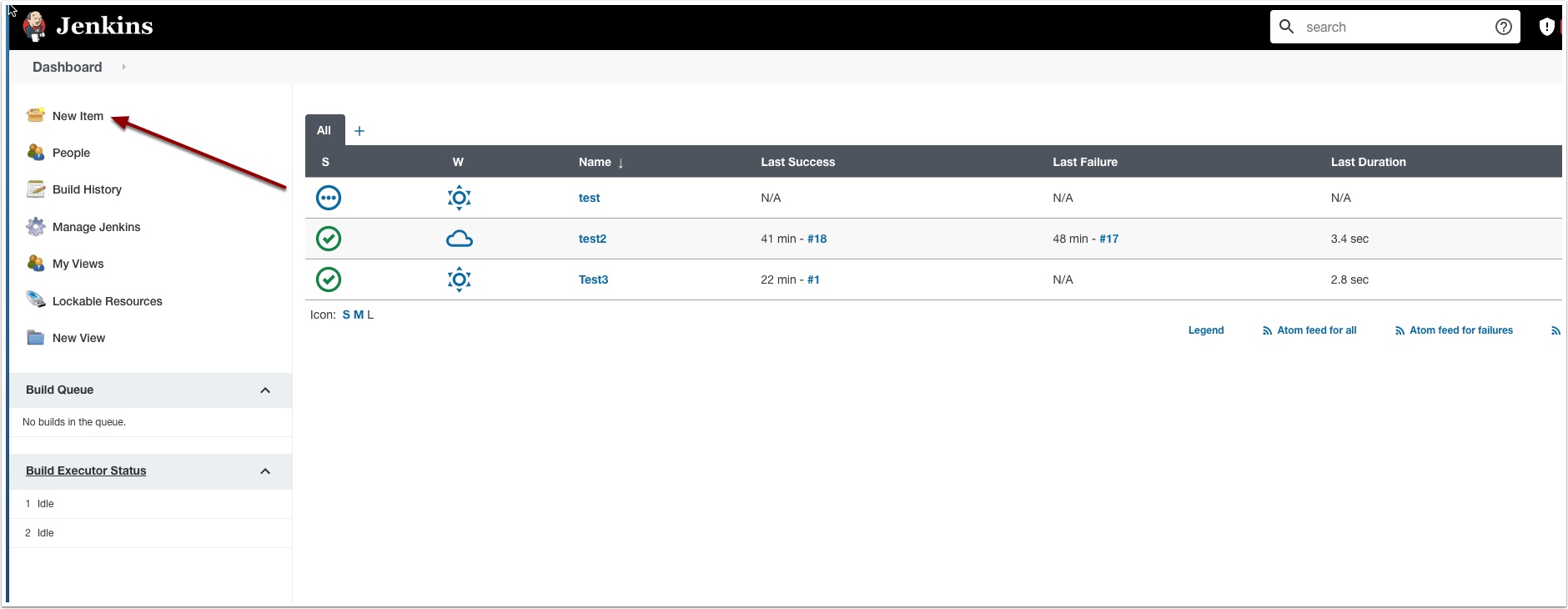
Now let’s create a new pipeline using our stored credentials
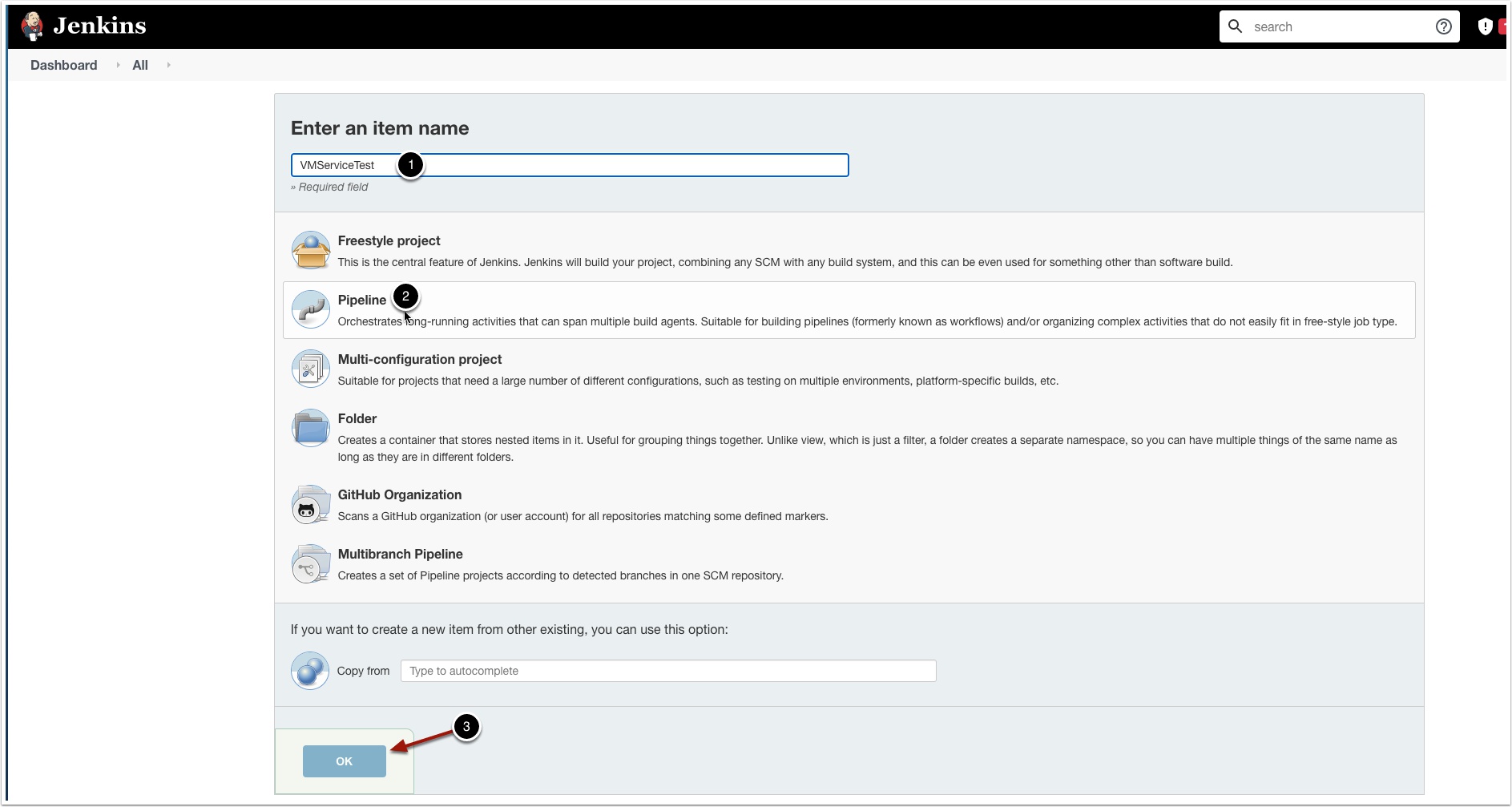
Click New Item
Configure the New Item
- Name the Item VMServiceTest
- Select Pipeline
- Click OK
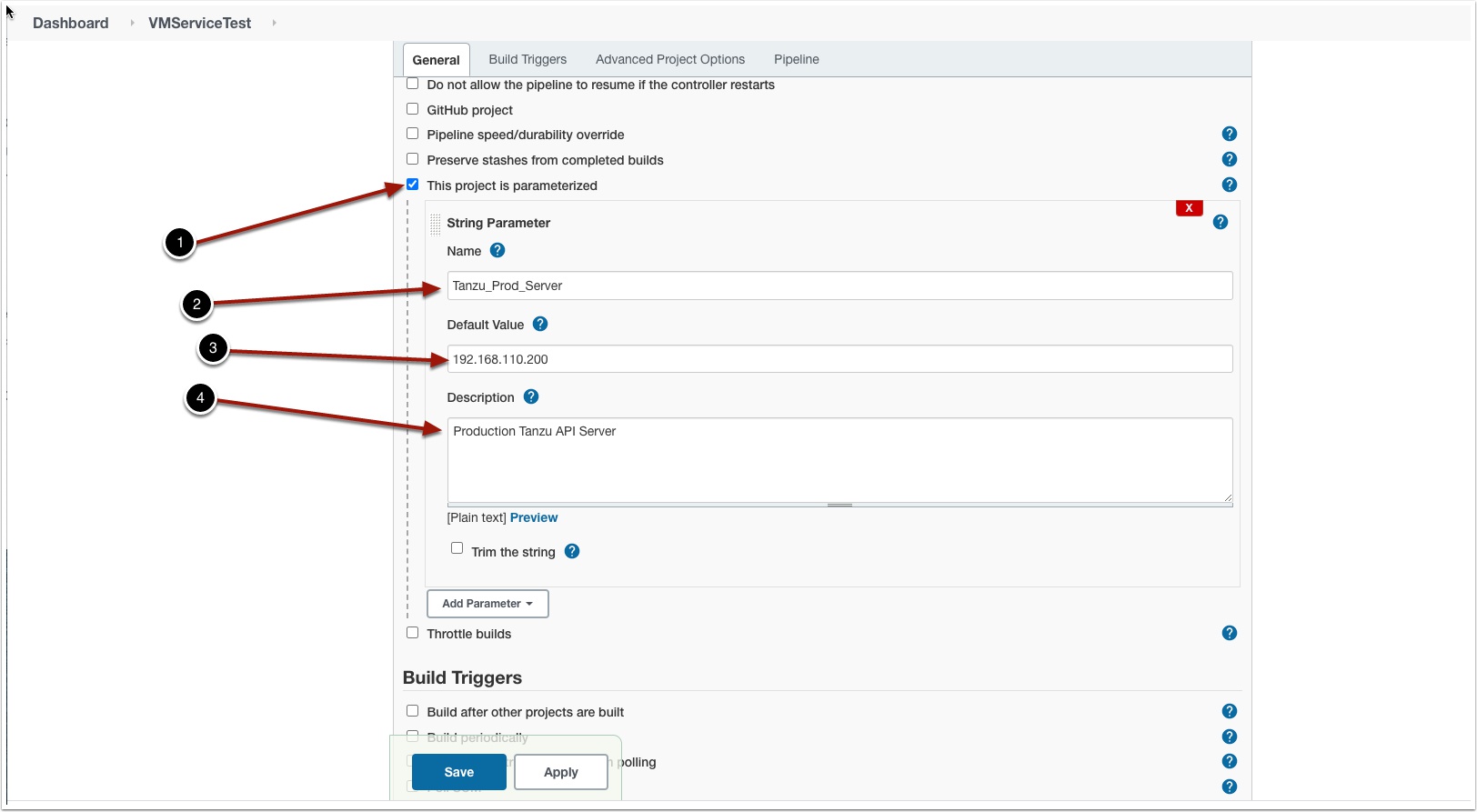
Create a Parameter for your Tanzu API server address
- Click the check box This project is parameterized
- Enter a name
- Enter the Tanzu API server FQDN or IP address
- Enter a description
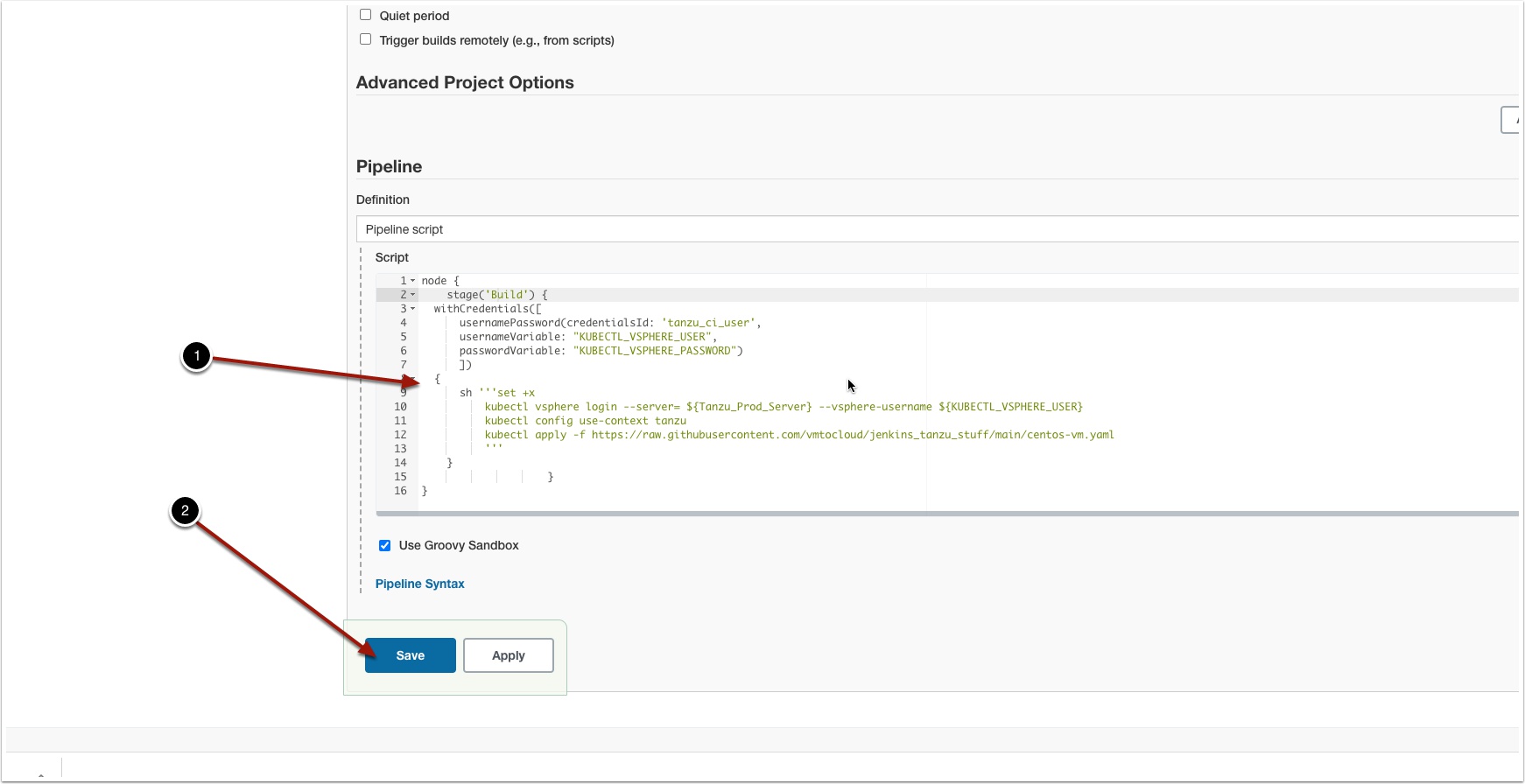
Scroll down to Pipeline Script and enter the following and click save (Note: I provided an example yaml file here on Github. You will need to create your own and point to it.
node {
stage('Build') {
withCredentials([
usernamePassword(credentialsId: 'tanzu_ci_user',
usernameVariable: "KUBECTL_VSPHERE_USER",
passwordVariable: "KUBECTL_VSPHERE_PASSWORD")
])
{
sh '''set +x
kubectl vsphere login --server= ${Tanzu_Prod_Server} --vsphere-username ${KUBECTL_VSPHERE_USER}
kubectl config use-context tanzu
kubectl apply -f https://raw.githubusercontent.com/vmtocloud/jenkins_tanzu_stuff/main/centos-vm.yaml
'''
}
}
}
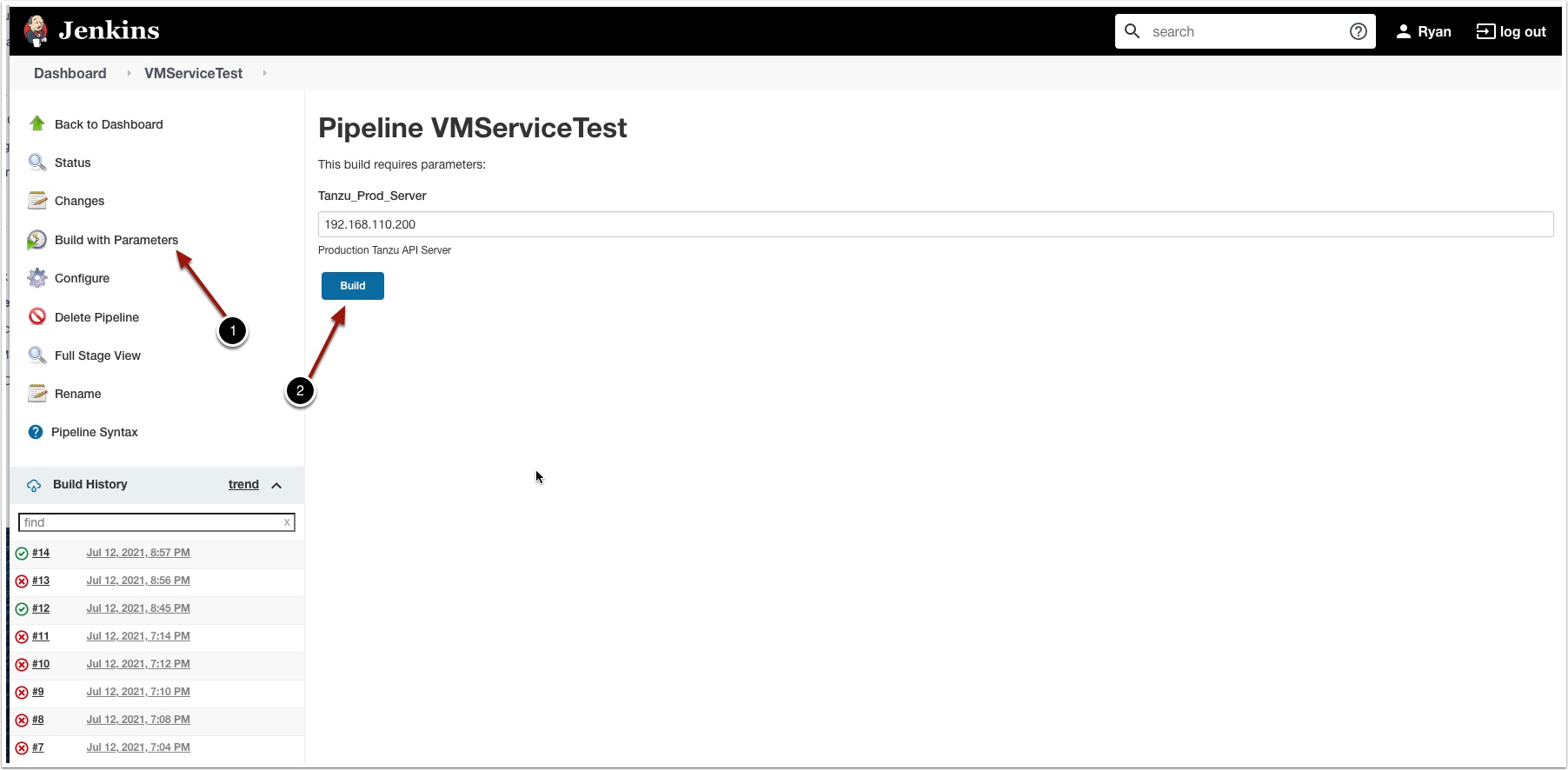
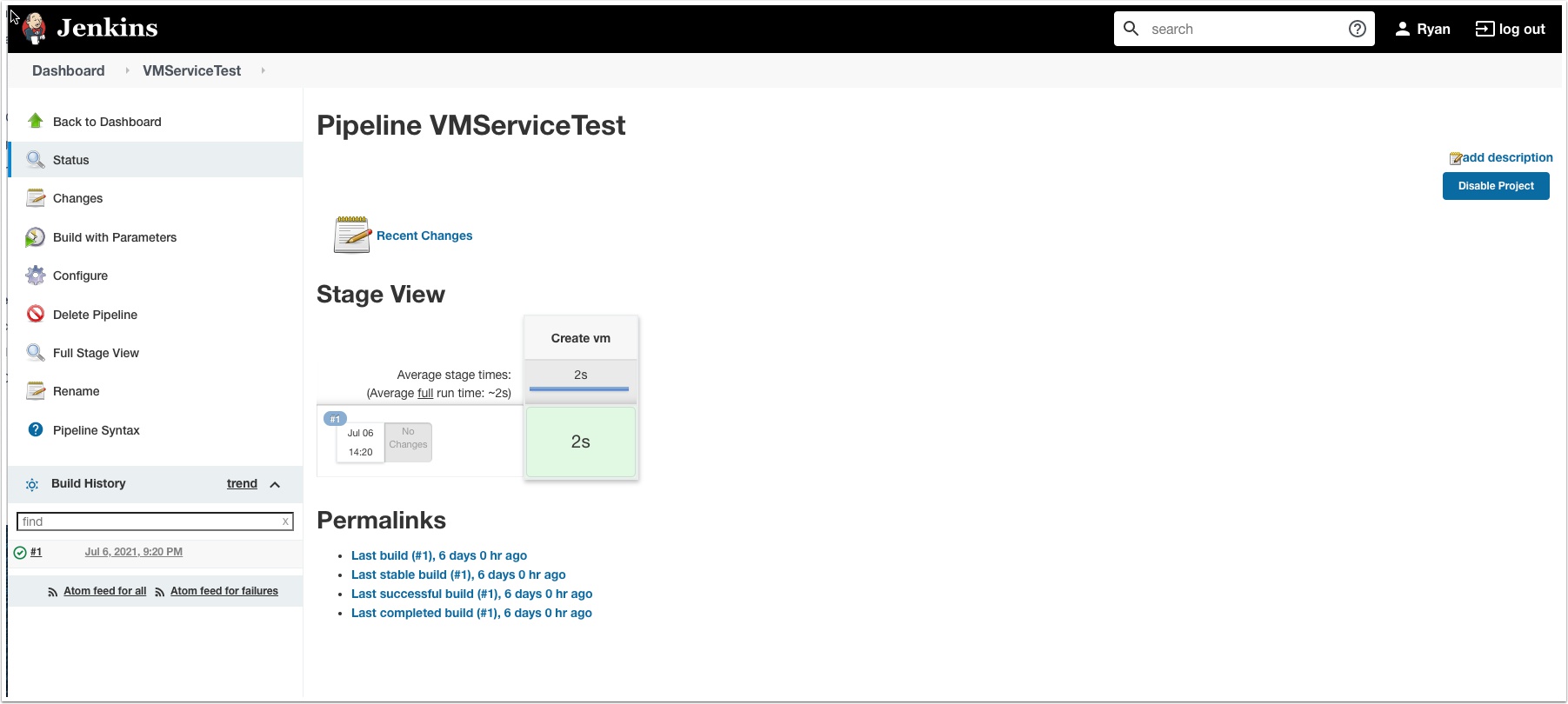
Click Build with parameters then click build. Notice now you could also change the Tanzu API server to Dev if you have one.
Click status and you should see the build is successful

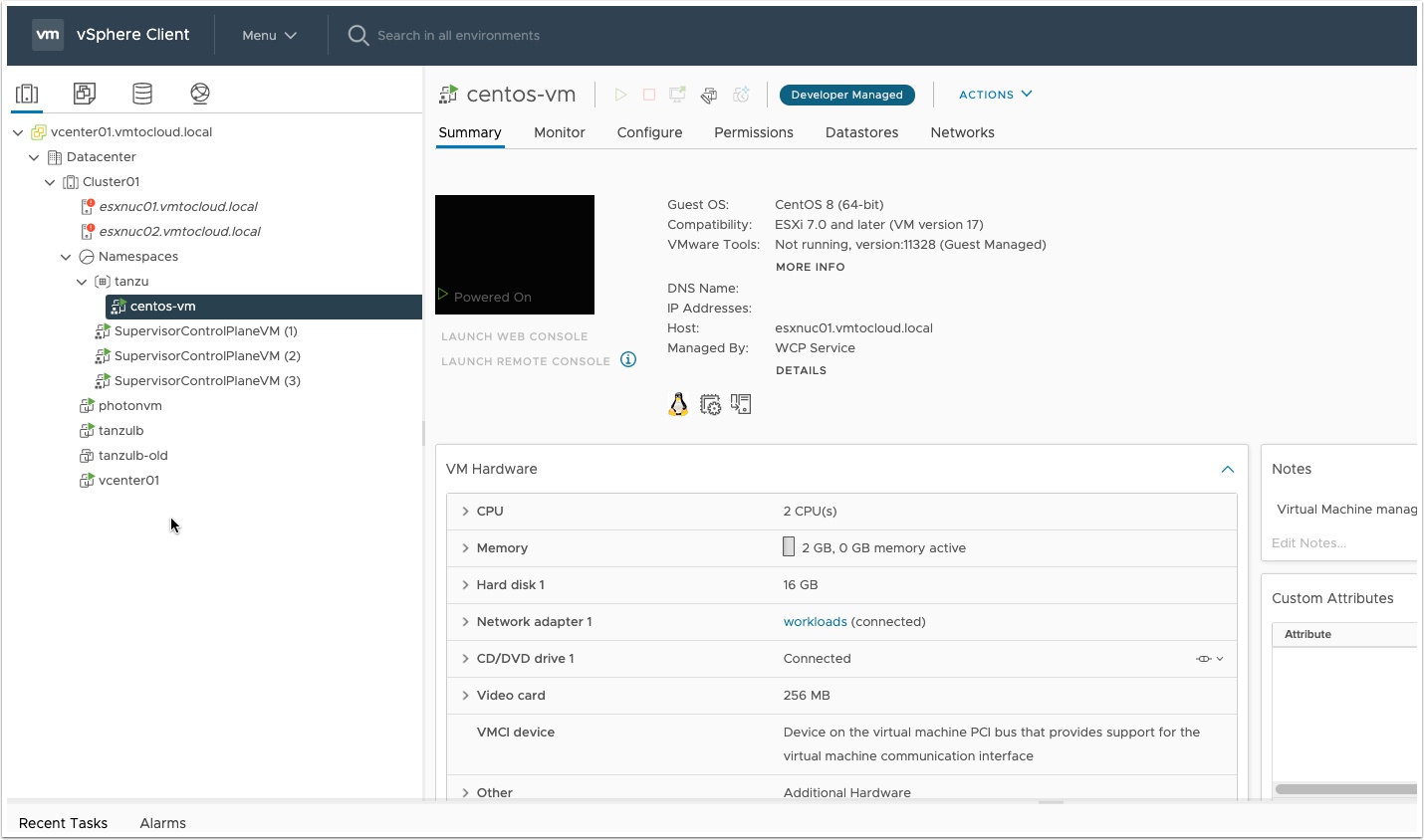
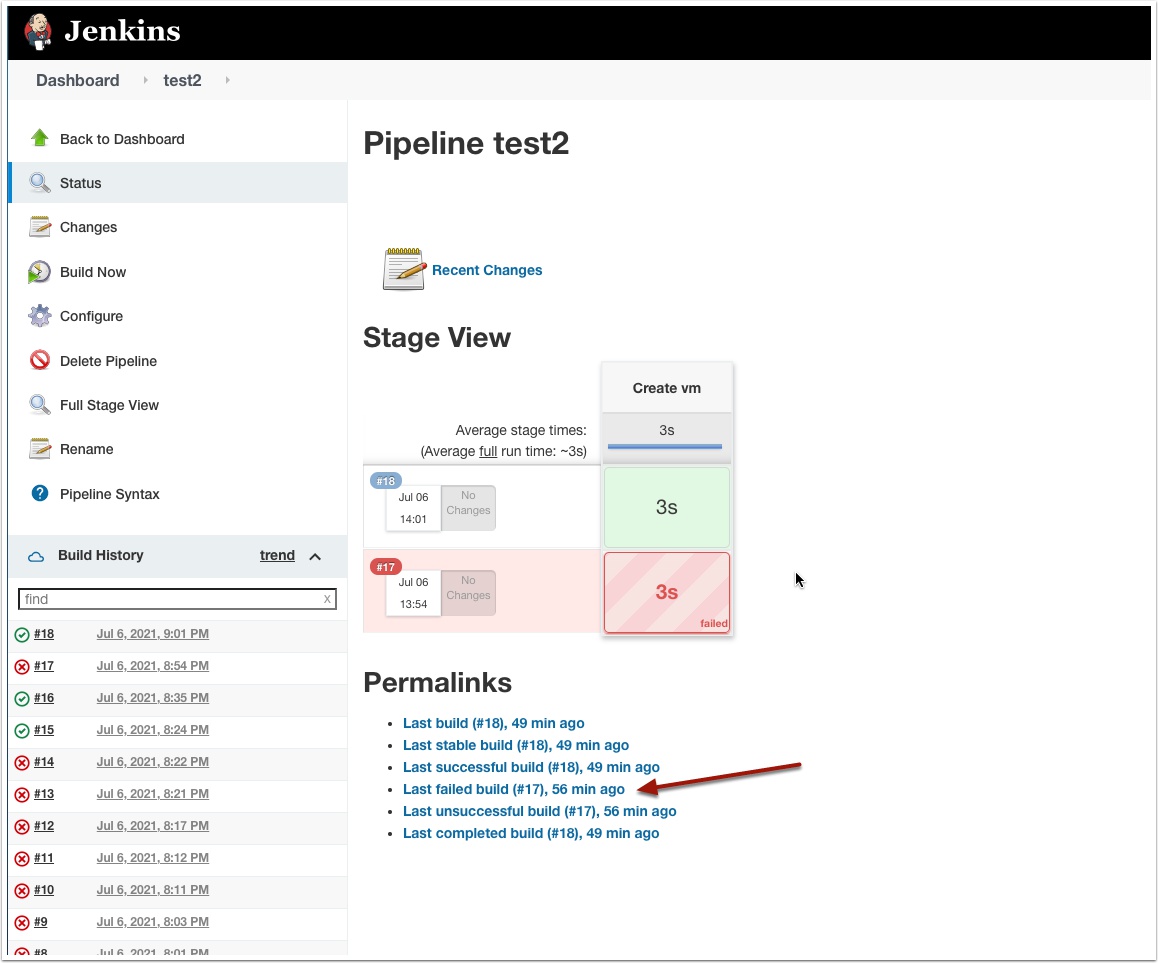
Wow, fantastic!!! It’s awesome. This is what I want exactly.
If I deploy pod using jenkins in tkg guest cluster, is there other better way than this post?
In some case, I used token of kubeconfig with integrated kubernetes plugin, but this token expired when reach out to 10 hours.